– Reading time: 13 minutes-
When I tell people that I’m passionate about hacking and cybersecurity, I often get asked, “Oh, so can you ‘hack’ anyone’s Instagram account you want?”. My answer, of course, is NO, or at least, IT DEPENDS. The problem is that hackers are often seen as mystical figures capable of effortlessly attacking any system or device. This idea is frequently fueled by movies where, in 90% of cases, scenes depict hackers compromising any system in just 10 seconds. How do they do it? By randomly pressing keys on the keyboard while uttering random technical terms, and strange things happen on the screen. For the viewer, the hacker’s image almost transforms into that of a magician. I don’t want to criticize such scenes too much; it’s understandable, especially if the movie in question doesn’t focus on cybersecurity – it’s ultimately cinematic fiction. However, you need to know that reality is quite different.
Let me be clear; I’m not downplaying a hacker’s abilities. Anyone who can effectively use a computer these days has incredible power. Nevertheless, carrying out such an attack is not as immediate as portrayed in movies. Everything follows a logical process, and there’s no magic sequence of commands that allows hacking a system in 10 seconds. In fact, there’s always a need for a planning/assessment phase where the target system is studied to understand how to execute the attack and what costs/risks it entails.
In this article, I’ll explain how such an attack could be planned, and by the end, you’ll understand why the answer to the initial question isn’t a simple YES. We’ll put ourselves in the shoes of a hacker, let’s call him Bob, who wants to steal another person’s Instagram profile, let’s call her Alice. We’ll explore the possible attack paths that Bob can take and evaluate the pros and cons of each. I’ll use Instagram as an example, but the insights I’ll share apply to any account you might want to target, from other social media platforms like Facebook, TikTok, and so on, to your online banking accounts.
IMPORTANT DISCLAIMER: This article is not an endorsement of any form of account theft. Unauthorized access to a system is a crime, aside from being ethically wrong. My goal is to inform you so that you can better protect yourself when it comes to this subject.
PLAN 1: Hacking Instagram
The idea I’ll explain in this paragraph probably represents the most challenging and risky path to choose for this type of attack. I’m mentioning it simply because people who don’t work in the field of cybersecurity, often influenced by what they see in movies, might think that hackers can easily gain access to a specific account by attacking Instagram itself. I want to encourage these individuals to understand what it means to “attack Instagram”. First and foremost, it’s essential to grasp where Instagram is physically located. I’m not referring to the app we’ve installed on our phones; that’s just the means through which we post new content, access content created by others, send and receive messages, and so on. But where is all that information stored? Who is responsible for storing all the posts, managing them, and ensuring that each of us can interact with them?
You should know that there’s a whole infrastructure of computers on the other side of the world that handles precisely this. There are servers that manage all our interactions with the social platform, large databases where all our data is gradually stored, and much more. Attacking Instagram would mean finding some vulnerability in this infrastructure that allows Bob to somehow access Alice’s account.
To be clear, I’m not suggesting that Bob should take a flight, go to Meta’s (the company that manages Instagram) headquarters, and physically access their computers. Of course, he could, but that would be insane. The more sensible approach would be to try to find such vulnerabilities remotely. Now, if Instagram were a small website with minimal security and numerous vulnerabilities, Bob might have considered this route. However, since this social platform is managed by Meta, one of the giants in the tech industry, I highly doubt there are easily discoverable vulnerabilities within it.
Certainly, nothing is impregnable, but why would Bob complicate his life so much? Planning such an attack would require a great deal of research, and there’s no guarantee he’d ultimately find points of entry. Moreover, attempting to hack such a massive company significantly increases the risk of being discovered. It wouldn’t be in Bob’s best interest to expose himself like that.
To help you better understand Bob’s reasoning, imagine being a thief and wanting to steal Alice’s money. Would you choose to rob her bank (with security guards, cameras, vaults, etc.), or would you look for a way to directly steal Alice’s credit card? Probably the latter, right? It’s the simpler and less risky option for your freedom. Why would you expose yourself so much if you only want to rob Alice? The logic is precisely the same: the smartest move to attack Alice’s Instagram account is to find a way to hack Alice herself.
PLAN 2: Guessing the Password
“A chain is only as strong as its weakest link”, and often the weakest link in a system is the person who controls it. That’s why in the previous paragraph, I told you that the smartest move to carry out the attack is to hack Alice: she is the weakest link.
The simplest route to take in this case is to try to guess her password. It may sound foolish, yet nowadays, this is a technique that could still work. Personally, I know many people who still use passwords like “FirstNameLastNameBirthDate”. After all, it’s the most convenient password one can use; it already contains all the known information, saving the “effort” of learning a new password. Unfortunately, such information is not difficult to uncover. Often, we leave traces on the web without even realizing it. By conducting the right online research, a hacker could obtain this information and, consequently, guess a password like that.
Of course, “FirstNameLastNameBirthDate” was just a simple example, but the same concept applies to passwords containing any of your other personal information and, quite plainly, even passwords like “12345”, “54321”, “qwerty”, “password”, etc. You probably already know the rules for a secure password: it should include a combination of uppercase letters, lowercase letters, numbers, and special characters (like !, @, #, $, %, etc.). The crucial thing that is often not emphasized is that such a password shouldn’t even resemble meaningful words. For example, if your dog’s name is Sophie, “$ophiE123456” is not a secure password, even though it contains numbers, special characters, lowercase, and uppercase letters.
Want an example of a secure password? Here it is: “iHRk@8$X_InO-!I8”. Could you easily remember the latter? The answer is, of course, NO, and that’s precisely why it’s perfect. If you don’t have easy ways to remember your password, it means that it would be impossible for any hacker to guess it. It might become unmanageable for you as well, but there are various programs that can assist you in managing such complex passwords so that you don’t even have to remember them. I might discuss these programs in a future article.
PLAN 3: Phishing
Suppose Alice has a secure password; in this case, Bob could try to leverage social engineering techniques. These techniques are based on manipulating human psychology and weaknesses to gain a specific advantage. Therefore, Bob could use social engineering to obtain access to Alice’s sensitive information through deceit, persuasion, or psychological manipulation. For example, by knowing Alice’s email address, Bob could send her a fake email pretending to be from the Instagram team with the goal of stealing her credentials. Such emails are called “phishing” emails. There are various messages that Bob could use for this purpose; the only limit is his imagination. A technique often used is to contact the victim with alarming messages to make them panic and act impulsively, following the attacker’s instructions without conducting due diligence. For instance, Bob could send Alice an email like this:
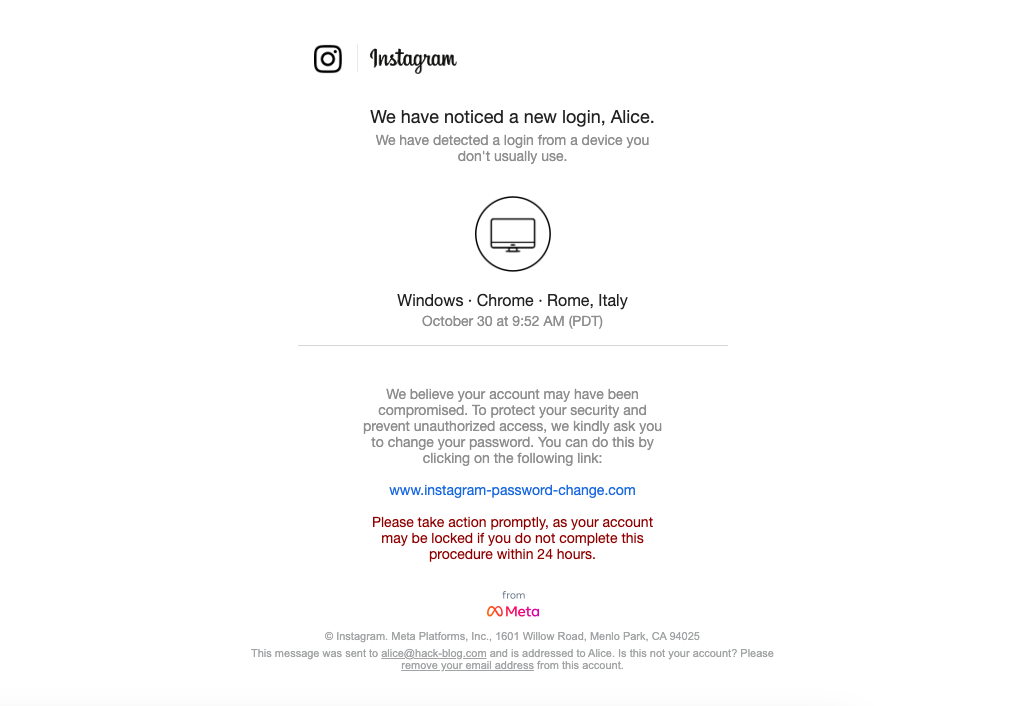
Let’s look at the email and put ourselves in Alice’s shoes. Alice sees that the email’s visual design is exactly the same as one Instagram would send. Once she clicks on the link, it opens what appears to be the official social media page. It truly seems that Instagram’s team sent this email. So why should Alice be meticulous and perform additional checks? They are asking her to enter her credentials within 24 hours; she needs to act quickly, or she’ll lose her account forever.
Upon accessing the link, the first thing Alice is asked for is her old credentials. It’s reasonable: the old credentials are used to confirm Alice’s identity before changing the password. Unfortunately, the link sent in the email leads to a site controlled by Bob, and by entering her credentials, Alice is sending them directly to her adversary. If Alice had thoroughly checked the email link received, tried to do a web search about it, she would have realized that, in reality, that website is not owned by Instagram.
Of course, I’m exaggerating the situation a bit because, as you’ll understand by the end of the article, these emails are not always as well-designed graphically. In general, however, one must always be prepared for even these extreme cases and be cautious of any email.
PLAN 4: Installing Malware
Suppose that this time, Alice has studied and learned not to click on email links. At this point, Bob could still use social engineering to try to install malware on Alice’s device through channels other than email. Specifically, Bob could find ways (which we’ll explore in future articles) to present Alice with messages that induce her to download a specific program.
Let’s imagine this scenario: Alice, while browsing the web, encounters a message like this: ‘We have detected malware on your device; download our antivirus immediately to resolve the issue’. Even in this situation, panic sets in. Alice starts to think that there’s a hacker who has managed to attack her smartphone and already feels like she’s being spied on. It needs to be resolved immediately, so she downloads the recommended antivirus, opens it, grants all the permissions, initiates the scan, and finally sees the message, ‘We have quarantined the malware named_a_fake_malware! Your device is now safe’. Alice heaves a sigh of relief and is pleased with the new antivirus she’s obtained.
Unfortunately, there never was any malware. Regrettably, the malware is the antivirus itself, and now Bob, who had planned it all, has full control of Alice’s phone and can discover everything she types (including her Instagram credentials). This time, Bob can even spy on her through the webcam and microphone; he can literally do anything with her phone.
PLAN 5: Wi-Fi Attacks
Another option is to find a way to connect to the same Wi-Fi network as Alice. You should know that under the same Wi-Fi network as the victim, various attacks can be executed. There’s not enough space today to explain these, but stay tuned because I will dedicate an entire article to it in the future.
So, to return to the initial question, at this point, it should be clear why the answer is not a simple YES. Everything depends on the person you want to target, how prepared they are, and how cautious they may be.
How to protect yourself from these attacks?
You should always pay the utmost attention to what you interact with on your screens. I’m not saying to become paranoid, but to give the right weight to certain things to avoid future problems. Here’s a list of rules you should always follow to use your devices safely:
- No matter what’s happening on your device, even if you receive an urgent message, stop, take a breath, and calmly analyze the situation. Always do this and never let anxiety take over!
- If you’re viewing a strange message, try searching for it on the web using a search engine. By doing so, you can see if anyone else received it before you.
- Check the grammar: in a genuine message, verbs will never be incorrect, and there will be no errors.
- Always analyze the visual aspect. In Plan 2, I showed you a visually perfect email, but attackers often don’t spend too much time fixing the graphics. Blurry images, imbalanced fonts can be red flags not to be underestimated.
- If you’ve been contacted via email, first check the sender’s address. Try doing a web search to see if it’s authentic.
- If the message you received pertains to Instagram, try accessing the original app to see if you’ve received a similar notification there. If you find the same message there, there might be a real problem. Otherwise, in an extreme situation, you could try contacting Instagram’s actual support for information.
- Always try to avoid clicking on strange links.
- If you’re somehow redirected to a suspicious website, always check the certificate by clicking on the padlock at the top of your browser. Verify the common name field and ensure it’s correct for the website you intend to visit.
- Be cautious about what happens on your device, especially when using public Wi-Fi.
- Never download any apps from your browser; trust (but not too much) only those from the official store for your device. Pay attention to the permissions requested when you download them: a legitimate antivirus probably won’t need permission to access your webcam or microphone.
- I’m sorry to say, but unfortunately, you can’t even trust your acquaintances completely. You must remain vigilant even if a strange message is sent by your father or mother. Am I telling you not to trust them? Absolutely not. I’m telling you not to trust their accounts and their phones. These could have been compromised in some way by a hacker. In this case, the hacker could exploit the trust you have in your relatives to make you lower your guard and attack your device as well.
- Enable two-factor authentication where you can; this way, even if a hacker manages to steal your credentials, they can’t access your accounts without the second factor.
- Use complex passwords (as explained in Plan 1) and use a different one for each service you use.
- Avoid giving personal information to strangers; sometimes even seemingly harmless details can be a crucial piece in the puzzle that the attacker is constructing.
In summary: never trust anyone!
In this article, I tried to provide you with some examples of how a hacker might attempt to steal a particular account. I listed various scenarios, but needless to say, imagination is the only limit to the possible paths a hacker could follow. Fortunately, phone manufacturers already consider many protections for their users, but unfortunately, this isn’t always enough. In general, you need to get used to thinking about your security personally, and following the advice I just gave can keep you at ease 99% of the time.